
The rapid transition of the global workforce to the home, as spurred on by the Covid-19 pandemic, has forced many organizations to overhaul their IT infrastructures, i.e. migrating to the cloud. This has allowed employees comfort while staying productive and efficient, as they work almost exclusively from home. A decade prior to that, Bring Your Own Device (BYOD) policies took hold and have swiftly become the standard.
Despite the tremendous benefits of cloud migration and BYOD policies for any organization, ultimately, they are bound to increase your risk of a data breach. This is because your team members now have access to sensitive company data at all times—not just when they are at work.
According to the research published in the 2021 Check Point Cyber Security Report, a new organization becomes a victim of ransomware every 10 seconds worldwide. Attacks on the healthcare sector have particularly become an epidemic as bad actors believe people in this sector are more inclined to pay ransoms, due to the pressures of Covid-19 cases.
Mobile devices are inherently vulnerable as was uncovered in Achilles where it was noted that over 400 vulnerable pieces of code were found within a Qualcomm DSP chip. This chip only powers millions of high-end smartphones from Samsung, Google, LG, etc. The significance of this cannot be understated with Qualcomm providing chips for over 40% of the mobile phone market.
An astounding 46% of organizations have had at least one employee download a malicious mobile application that threatened networks and data. This is a prominent threat that could put your organization out of business depending on what files and information got compromised. You need a plan for when ‘everyday disasters’ occur.
Enter Mobile Device Management. What Is It Exactly?
Mobile Device Management (MDM) optimizes the privacy, safety, and functionality of all mobile devices within your organization. This includes monitoring, managing, and protecting data across online-based infrastructures, applications, and platforms. Securing these systems involves the collaborative efforts of a reputable Managed Service Provider (MSP) and the end-users in your organization. Understanding both facets is pivotal to a healthy cloud security solution.
At its core, cloud security is comprised of the following categories:
- Safe Remote Access. An MDM layer provides users remote access to corporate applications from their mobile workspaces using their smartphones, tablets, laptops, and PCs. Additionally, mobile application management can also be implemented to control access to company data based on what mobile apps are on your phone, what apps aren’t, and what apps you want to permit your employees to access and use. It also protects your company from the ongoing threats of malware and data breaches by blocking unsafe websites and material from use. It’s almost impossible to police what sites your team members are surfing, so let your MSP do it for you.
- Policies on Threat Prevention, Detection, and Mitigation. With TNS’ endpoint protection technology, employers can manage secure policies such as encryption, passcodes, data loss, prevention, remote lock and wipe and patch management to keep data protected across all users.
- Business Continuity and Data Recovery Planning. MDM can remotely lock and wipe all data in case a mobile device is lost or stolen. In case of a natural disaster, cyber attack, and human error, your MSP will ensure that your data can have both a cloud backup while also being stored in a data center.
Your data is the lifeblood of your organization and keeping it protected should not be an afterthought.
The cost savings and flexibility of cloud computing does not outweigh the results of losing sensitive company information. Depending on what kind of organization you are, this could result in hefty fines as well. With MDM software an MSP will act as your personal mobile operator and allow you to harness the benefits of the cloud without discounting the security of your data.
Microsoft Cloud App Security
Microsoft Cloud App Security allows for advanced Data Loss Prevention (DLP) policies that can be applied at the folder or file level. For example, if someone logs in on EST at 2 pm and then logs in on the west coast, it will be flagged. It natively integrates with your Microsoft and third party cloud services to provide simple deployment, centralized management, and innovative automation capabilities. It works by improving visibility of cloud activity and helping to increase the protection of corporate data.
The Cloud App Security Framework’ Benefits at a Glance
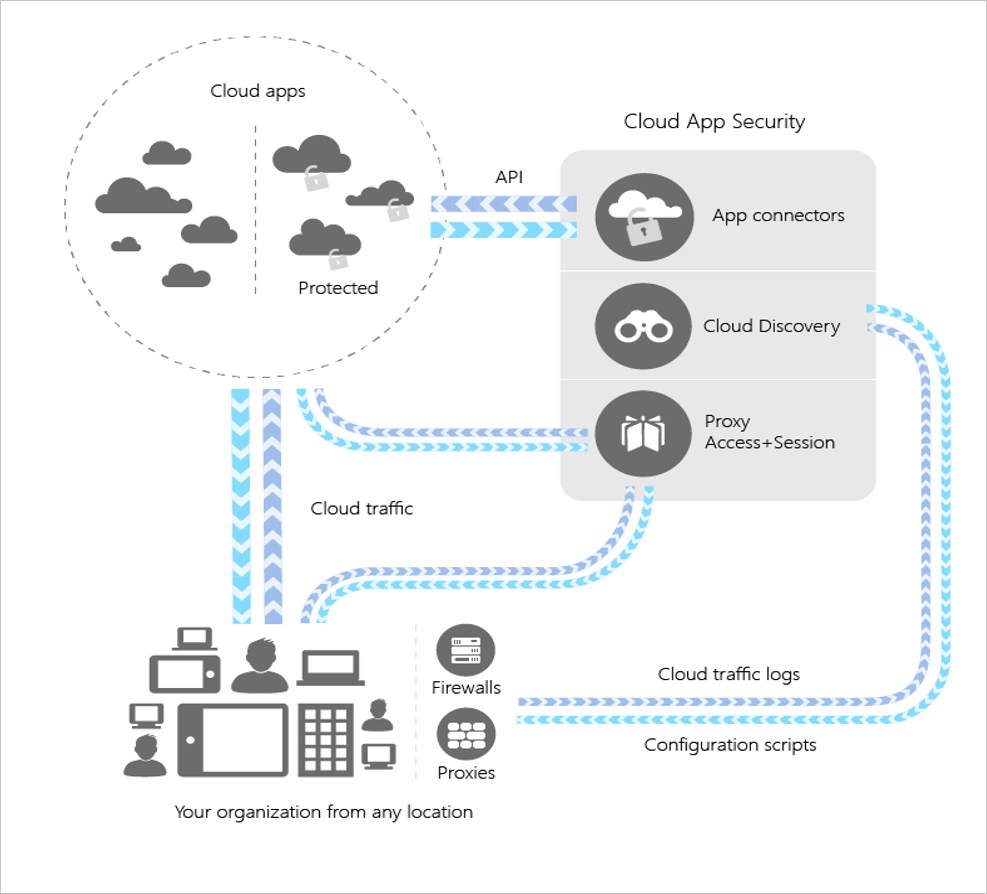
- Sanction or unsanction apps in your organization by using the Cloud App Catalog—an extensive and continuously growing catalog of over 16,000 cloud apps that are ranked and scored based on industry standards. Based on these scores, Cloud App Security lets you know how risky an app is.
- With Conditional Access App Control, you can avoid data leaks by blocking downloads before they happen.
- Set rules that force data stored in and downloaded from the cloud to be protected with encryption.
- Gain visibility into unprotected endpoints so you can monitor what's being done on unmanaged devices.
- Control access from non-corporate networks or risky IP addresses.
- Identify high-risk usage and security incidents, detect abnormal user behavior, and prevent threats.
- You can use policies to define your users' behavior in the cloud. Use policies to detect risky behavior, violations, or suspicious data points and activities in your cloud environment. Types of policies correlate to the different types of information you might want to gather about your cloud environment and the types of remediation actions you might take.
A Call-To-Action
There is no shortage of mobile devices in today’s business world. This increased use during global lockdowns has especially made these devices moving targets of cyber-attacks. Threat actors will continue to exploit the disruption caused by the Covid-19 pandemic to target organizations across all sectors.
Are you looking to implement a Mobile Device Management Solution in your organization? Contact The TNS Group today to stay on top of data breaches.
Categories: Managed Service Provider, MSP Blogs




